arcanicanis on Nostr: So here’s an example of one of the maliciously-crafted payloads that resulted in a ...
So here’s an example of one of the maliciously-crafted payloads that resulted in a 9.8 severity CVE (CVE-2024-23832) against Mastodon:
{
"@context": ["
https://www.w3.org/ns/activitystreams";],
"id": "
https://mastodon.social/users/Gargron/posts/123456";,
"type": "Note",
"actor": "
https://mastodon.social/users/Gargron";,
"attributedTo": "
https://mastodon.social/users/Gargron";,
"content": "Well, this is an extremely concerning vulnerability I should have accounted for.",
"to": [ "
https://www.w3.org/ns/activitystreams#Public"; ],
"cc": [ "
https://mastodon.social/users/Gargron/followers"; ],
"published": "2024-01-28T22:00:00Z"
}
I have previously double-checked with one of the Mastodon developers (while CC’ing the Mastodon Security email) to confirm that I’m free to release the details at this scheduled time (Feb 15th 15:00 UTC). According to the current observed metrics on FediDB, >73.6% of Mastodon instances are patched against CVE-2024-23832, as manually tabulated.
For more details on the vulnerability, the original security report as it was submitted on Github is available at:
https://arcanican.is/excerpts/cve-2024-23832/My recount of events (as well as unsolicited commentary and criticisms on the vulnerability, ecosystem, etc; when I get around to finishing it):
https://arcanican.is/excerpts/cve-2024-23832/discovery.htm 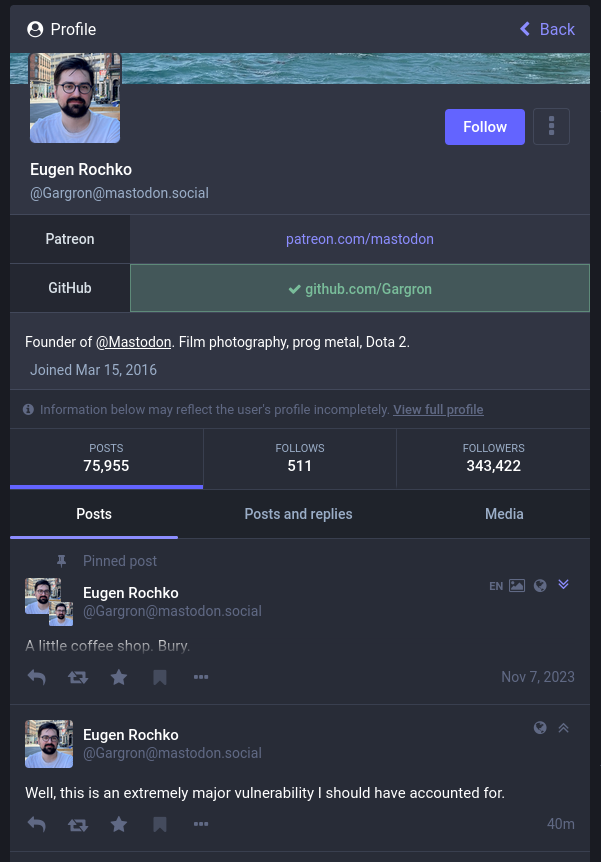
Published at
2024-02-15 15:00:00Event JSON
{
"id": "43bfa18bdbe0263b911d796da3f6b9c681efc3413e9e08ca85fd60fed473e212",
"pubkey": "0ed7afc8b04a4ef5d52c14fd46c65e452d62ca50a47d6cf5287ed2825a6d26f7",
"created_at": 1708009200,
"kind": 1,
"tags": [
[
"proxy",
"https://were.social/objects/cfe6a3fd-17d5-439f-b81a-7d750baca280",
"activitypub"
]
],
"content": "So here’s an example of one of the maliciously-crafted payloads that resulted in a 9.8 severity CVE (CVE-2024-23832) against Mastodon:\n\n{\n \"@context\": [\"https://www.w3.org/ns/activitystreams\"],\n \"id\": \"https://mastodon.social/users/Gargron/posts/123456\",\n \"type\": \"Note\",\n \"actor\": \"https://mastodon.social/users/Gargron\",\n \"attributedTo\": \"https://mastodon.social/users/Gargron\",\n \"content\": \"Well, this is an extremely concerning vulnerability I should have accounted for.\",\n \"to\": [ \"https://www.w3.org/ns/activitystreams#Public\" ],\n \"cc\": [ \"https://mastodon.social/users/Gargron/followers\" ],\n \"published\": \"2024-01-28T22:00:00Z\"\n}\n\nI have previously double-checked with one of the Mastodon developers (while CC’ing the Mastodon Security email) to confirm that I’m free to release the details at this scheduled time (Feb 15th 15:00 UTC). According to the current observed metrics on FediDB, \u003e73.6% of Mastodon instances are patched against CVE-2024-23832, as manually tabulated.\n\nFor more details on the vulnerability, the original security report as it was submitted on Github is available at: https://arcanican.is/excerpts/cve-2024-23832/\n\nMy recount of events (as well as unsolicited commentary and criticisms on the vulnerability, ecosystem, etc; when I get around to finishing it): https://arcanican.is/excerpts/cve-2024-23832/discovery.htm\n\nhttps://were.social/media/6ff54bdc52e5011feb9b11a715a0e4206060a10b523d864814345a3fc7f9734c.png\n\nhttps://were.social/media/c0bf24a97dec84fbbc9c22244334160c7b056d29b03ab180bae6d2bb57455441.png",
"sig": "679192ca0ddf43128d065d6bd68aaa9d9f290c1f0a1e081a82acebd310c9a3728a7deb1fcb2bf488ee6efcc973f934b1751bfc4d32ba6e4358db5538617ea4bb"
}


