final [GrapheneOS] 📱👁️🗨️ on Nostr: An iPhone and stock Pixel are around the same, but Pixels obviously gives you more ...
An iPhone and stock Pixel are around the same, but Pixels obviously gives you more freedom of apps, while Apple's online services are arguably better. There are pros and cons. You're at the bane of either Google or Apple if you use their services. For iPhone, Lockdown Mode exists for added security too but it messes with some browser and messenger functionality. Pixels let you install other OSes safely and easily which is where more private and secure options like ours can be installed onto.
https://grapheneos.org/GrapheneOS runs on Pixels because they are the highest security platform commercially available to us. For other Android platforms, Samsung comes close but destroys hardware and security functionality on other OSes by an eFuse so we can't use them. Most other Android devices are insecure by being slow on updates and patches or with their hardware choices. Google quickly responds to our vulnerability reports while some haven't even tried to deal with issues we believe affect several other devices that we reported several months ago.
Pixel 8 and later are the best of them as they have hardware security features like MTE which previous generations don't have. They also get security updates for 7 years since launch. We are always open to working with other device manufacturers to hopefully go above what Pixel offers, or to provide an alternative. Most times they fall through because they want to do something different. We have strict demands.
Cellebrite Premium (phone extraction tool exclusive to police) documents say they can do iPhone access on every iPhone on latest iOS while for Pixels they can only hit the stock OS (not GrapheneOS who they DIRECTLY mention) and they cannot brute force the secure element. The stock OS on Pixels does not take full advantage of the security features available to them, like MTE, which is a game changer.
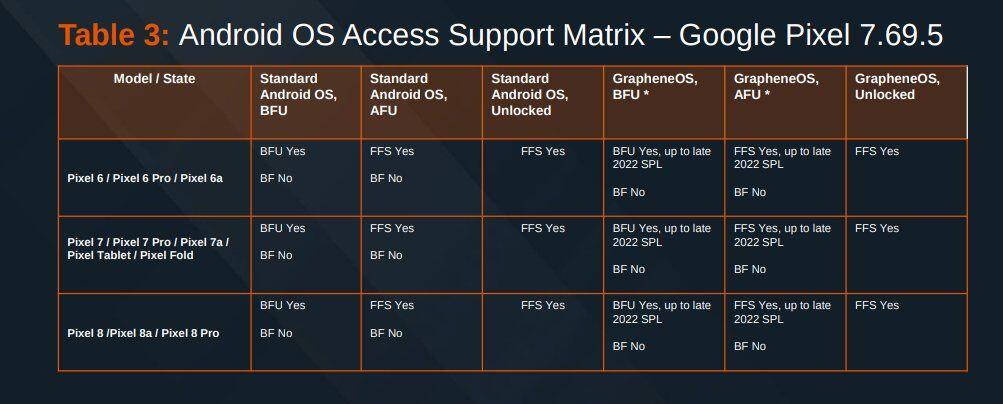
The Cellebrite docs provide a good insight on what device companies with massive budget have a harder time in exploiting:
EXCLUSIVE: Here's the Cellebrite Premium 7.69.5 iOS Support Matrix from July 2024.
404media recently published an article based on the same April 2024 docs we received in April and published in May. Many tech news sites including 9to5Mac made incorrect assumptions treating that as current.
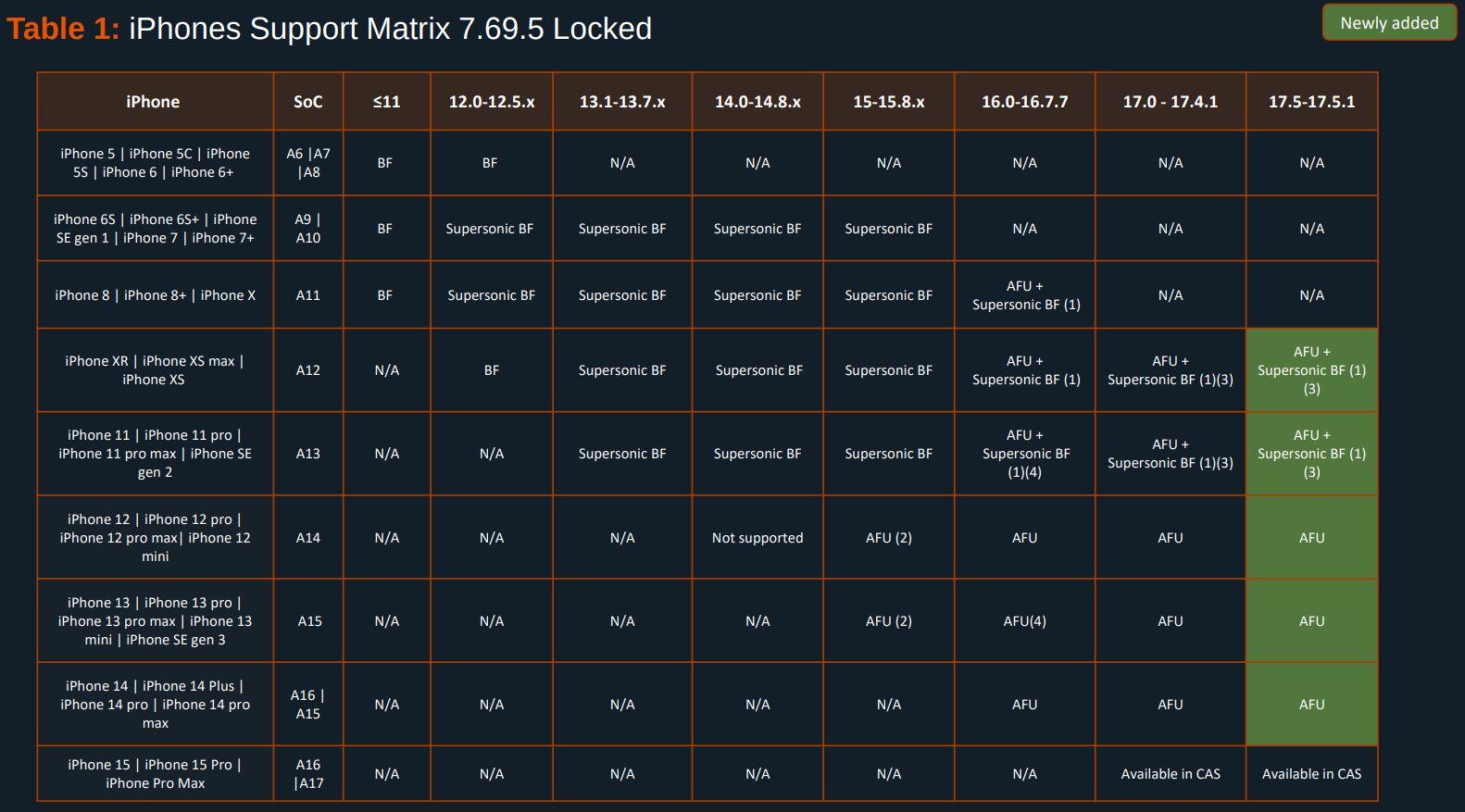
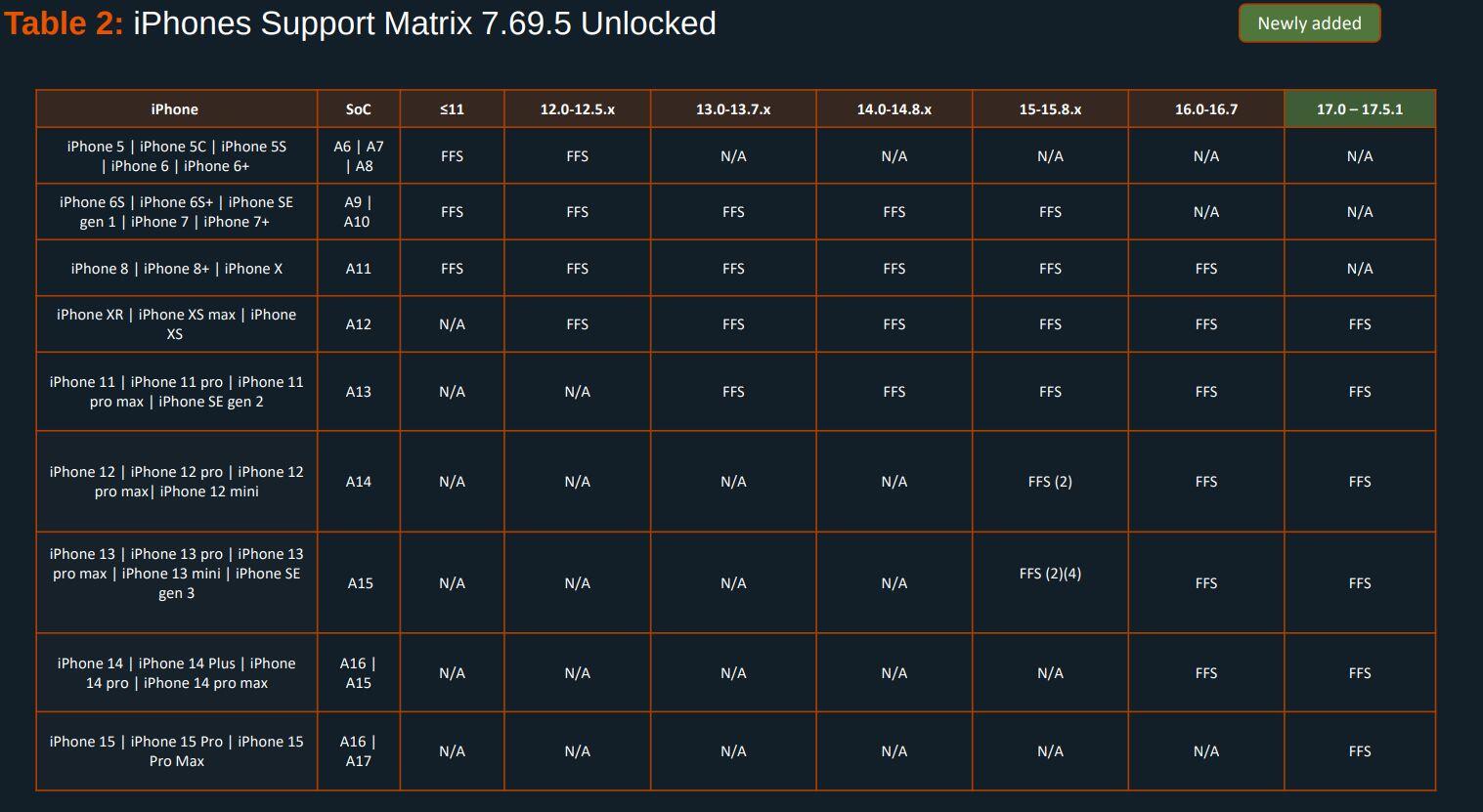
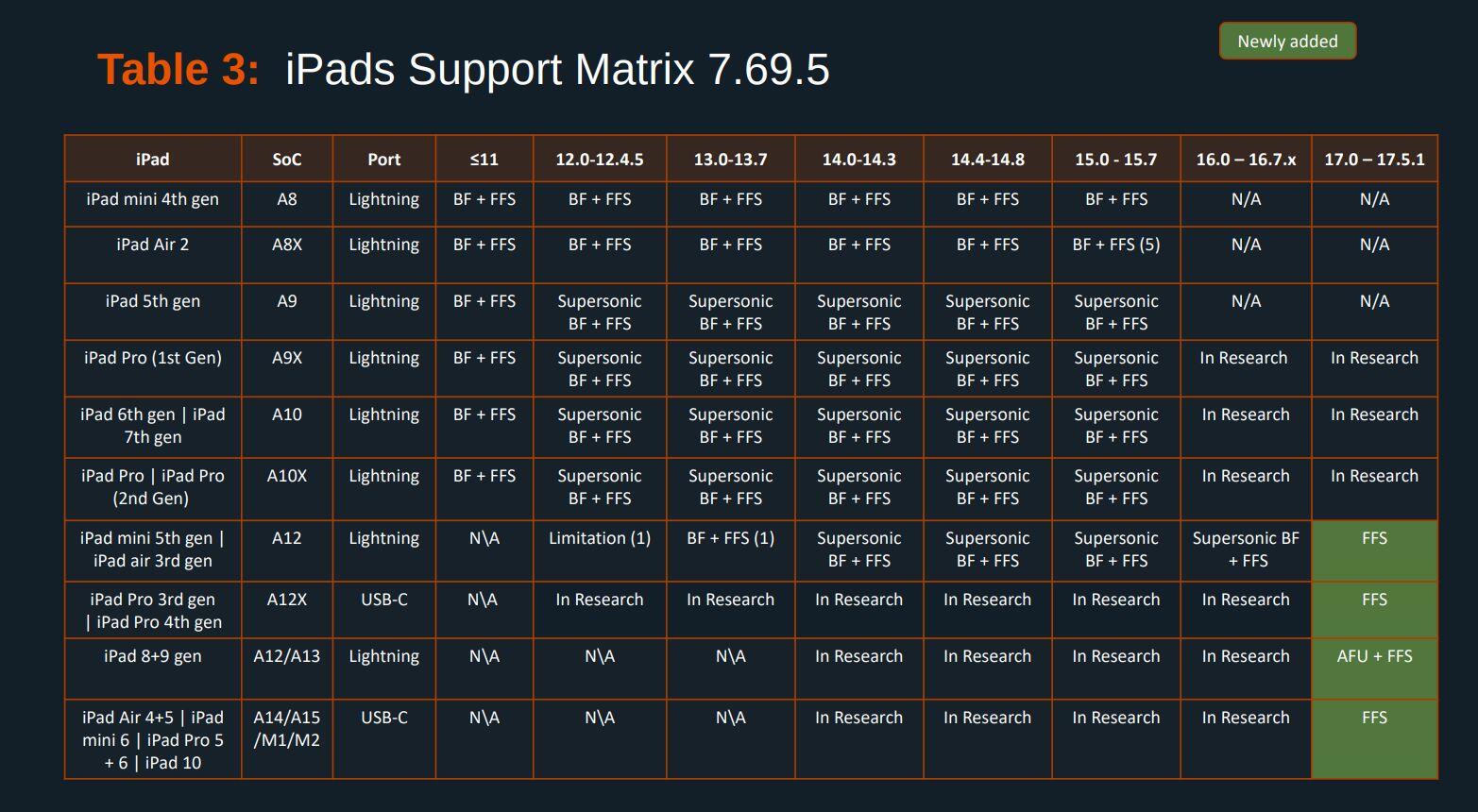
Here's the Cellebrite Premium 7.69.5 Android Support Matrix from July 2024 for Pixels. They're still unable to exploit locked #GrapheneOS devices unless they're missing patches from 2022. A locked GrapheneOS device also automatically gets back to BFU from AFU after 18h by default.
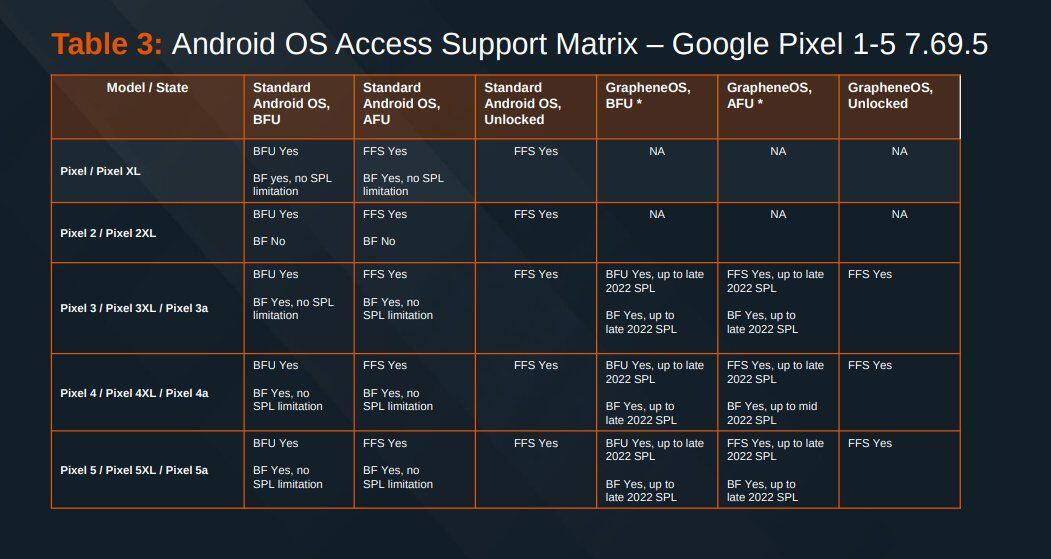
Obviously it doesn't completely deny possibility of attacks. Technology is not impenetrable and people who think very powerful organisations is after them need to behave differently too.
Published at
2024-08-25 14:21:51Event JSON
{
"id": "807fa9b3dd8d0b50539effb4502185750d87a95f72a31704ab34ccb374ba3be1",
"pubkey": "c15a5a65986e7ab4134dee3ab85254da5c5d4b04e78b4f16c82837192d355185",
"created_at": 1724595711,
"kind": 1,
"tags": [
[
"e",
"d1c033053ef046d246ce80fc9920e586c30372252a4482a2362648d92a17b833",
"",
"root"
],
[
"e",
"43bb22c3b67cf123ce5b83eb26c4573434a879f36c4c1aa8b63c051e1ef92b54"
],
[
"e",
"f991d98ce6dd92871279914d60083921ebfc1533ac190ad112c2173af1f3d55b",
"",
"mention"
],
[
"e",
"f492c91408da992b553435b985f04f256b52c86b7601eae719842a2ea5a5d3c7",
"",
"reply"
],
[
"p",
"c15a5a65986e7ab4134dee3ab85254da5c5d4b04e78b4f16c82837192d355185",
"",
"mention"
],
[
"p",
"76b59ceb3a7a97e8fd25b761f72c96e9648c627d01d0f766f0b2eec6ebd079f3"
],
[
"q",
"f991d98ce6dd92871279914d60083921ebfc1533ac190ad112c2173af1f3d55b"
],
[
"r",
"https://grapheneos.org/"
]
],
"content": "An iPhone and stock Pixel are around the same, but Pixels obviously gives you more freedom of apps, while Apple's online services are arguably better. There are pros and cons. You're at the bane of either Google or Apple if you use their services. For iPhone, Lockdown Mode exists for added security too but it messes with some browser and messenger functionality. Pixels let you install other OSes safely and easily which is where more private and secure options like ours can be installed onto.\n\nhttps://grapheneos.org/\n\nGrapheneOS runs on Pixels because they are the highest security platform commercially available to us. For other Android platforms, Samsung comes close but destroys hardware and security functionality on other OSes by an eFuse so we can't use them. Most other Android devices are insecure by being slow on updates and patches or with their hardware choices. Google quickly responds to our vulnerability reports while some haven't even tried to deal with issues we believe affect several other devices that we reported several months ago.\n\nPixel 8 and later are the best of them as they have hardware security features like MTE which previous generations don't have. They also get security updates for 7 years since launch. We are always open to working with other device manufacturers to hopefully go above what Pixel offers, or to provide an alternative. Most times they fall through because they want to do something different. We have strict demands.\n\nCellebrite Premium (phone extraction tool exclusive to police) documents say they can do iPhone access on every iPhone on latest iOS while for Pixels they can only hit the stock OS (not GrapheneOS who they DIRECTLY mention) and they cannot brute force the secure element. The stock OS on Pixels does not take full advantage of the security features available to them, like MTE, which is a game changer.\n\nThe Cellebrite docs provide a good insight on what device companies with massive budget have a harder time in exploiting:\n\nnostr:nevent1qqs0nywe3nndmy58zfuezntqpqujr6luz5e6cxg26yfvy9e678ea2kcpz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygxptfdxtxrw026pxn0w82u9y4x6t3w5kp883d83djpgxuvj6d23s5psgqqqqqqs0femts\n\nObviously it doesn't completely deny possibility of attacks. Technology is not impenetrable and people who think very powerful organisations is after them need to behave differently too.",
"sig": "642d66c16a90b66a2ff432f943c7f2f3d90a3467b707cb321bf3a025d82101d37a1c6945a9f51eaaf4b0189f89ae9f3acbe48f88dc8bc3b82c233354b9108c8c"
}





